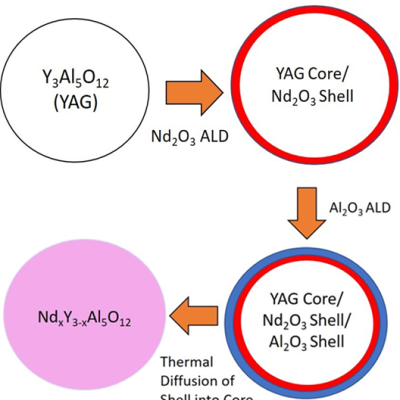
Powder atomic layer deposition process is used to coat nanopowders of host materials (e.g. yttrium aluminum garnet) with optically active neodymium organometal precursor followed by O2/O3 RF plasma to convert to a single layer of Nd2O3. The process can be repeated to build arbitrarily thick layers with custom doping profiles and followed by post-…
Keywords
- Show all (240)
- Additive Manufacturing (55)
- Instrumentation (41)
- Synthesis and Processing (21)
- Sensors (14)
- Diagnostics (11)
- Imaging Systems (9)
- Photoconductive Semiconductor Switches (PCSS) (9)
- 3D Printing (8)
- Carbon Utilization (7)
- Electric Grid (7)
- Materials for Energy Products (7)
- Semiconductors (7)
- Substrate Engraved Meta-Surface (SEMS) (7)
- Therapeutics (7)
- Compact Space Telescopes (6)
- Brain Computer Interface (BCI) (5)
- Data Science (5)
- Diode Lasers (5)
- Optical Switches (5)
- (-) Laser Materials Processing (4)
Technology Portfolios

This invention proposes using a pulse laser configured to generate laser pulses and a controller for controlling operation of the pulse laser. The controller is further configured to control the pulse laser to cause the pulse laser to generate at least one of the laser pulses with a spatiotemporally varying laser fluence over a duration of at least one of the laser pulses. The spatiotemporally…

CSP-POST provides the capability to inspect all incoming and outgoing emails while providing after-the-fact forensic capabilities. Using commercially available lightweight and serverless technologies, CSP-POST easily collects all email and parses it into easily searchable metadata, enriched and ready for analysis. The web-based application is deployed in a repeatable, testable, and auditable…

LLNL has invented a new system that uses public key cryptography to differentiate between human-generated text and AI-generated text. This invention can be used to validate that text is likely to be human generated for the purposes of sorting or gatekeeping on the internet, can detect cheating on essay assignments, and can be used as an automatic captcha that does away with the hassle of…

LLNL has developed a new method for securely processing protected data on HPC systems with minimal impact on the existing HPC operations and execution environment. It can be used with no alterations to traditional HPC operations and can be managed locally. It is fully compatible with traditional (unencrypted) processing and can run other jobs, unencrypted or not, on the cluster simultaneously…

The new LLNL technique works by transiently removing and trapping concrete or rock surface material, so that contaminants are confined in a manner that is easy to isolate and remove. Our studies suggest that 10 m2 of surface could be processed per hour. The technique easily scales to more surface/hr.