This invention works by imaging an ultrafast pulse diffracted from a large grating onto a spatial light modulator (SLM) thereby directly transcribing an arbitrary record on a pulse front tilted (PFT) ultrafast pulse. The grating generates PFT of the input pulse, and the SLM provides temporal control of the pulse through the space-to-time mapping of the tilted pulse. Coupling this patterned…
Keywords
- Show all (68)
- Electric Grid (8)
- Carbon Utilization (6)
- Compact Space Telescopes (5)
- Data Science (5)
- Laser Materials Processing (5)
- Diode Lasers (4)
- Materials for Energy Products (4)
- Optical Damage Mitigation (3)
- 3D Printing (2)
- Additive Manufacturing (2)
- Computing (2)
- Direct Air Capture (2)
- Imaging Systems (2)
- Power Electronics (2)
- Simulation (2)
- Synthesis and Processing (2)
- Ultrashort Pulse Lasers (2)
- (-) Cybersecurity (4)
- (-) Precision Optical Finishing (3)
- (-) RF Photonics (3)
Technology Portfolios
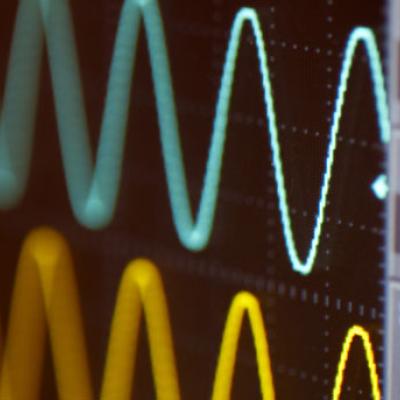
This invention exploits the non-linearities of optical Mach-Zehnder (MZ) electrooptic modulators to enhance small signal dynamic range at higher bandwidths. A linear photodiode (PD) converts the amplified optical signal output from the MZ back to an electrical signal completing an Electrical-Optical-Electrical (EOE) conversion cycle. The dynamic range can be further enhanced by daisy chaining…
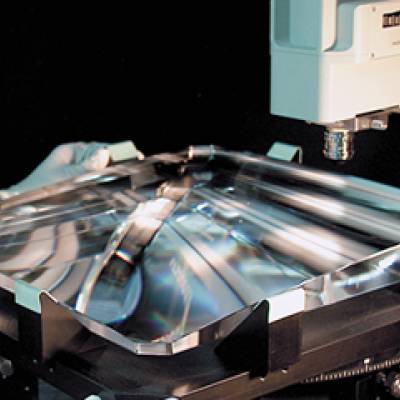
This invention takes advantage of the high water-solubility of key NIF KDP crystal optics and uses water as an etchant to remove surface defects and improve the laser induced damage threshold. Since pure water etches KDP too fast, this invention is to disperse water as nanosized droplets in a water-in-oil micro-emulsion. While in a stable micro-emulsion form, the surfactant additives prevent…
This invention proposes to use laser induced melting/softening to locally reshape the form of a glass optic. The local glass densification that results induces predictable stresses that through plate deformation mechanics yield a deterministic methodology for arbitrarily reshaping an optic surface figure and wavefront without the need to remove material.

CSP-POST provides the capability to inspect all incoming and outgoing emails while providing after-the-fact forensic capabilities. Using commercially available lightweight and serverless technologies, CSP-POST easily collects all email and parses it into easily searchable metadata, enriched and ready for analysis. The web-based application is deployed in a repeatable, testable, and auditable…

LLNL has invented a new system that uses public key cryptography to differentiate between human-generated text and AI-generated text. This invention can be used to validate that text is likely to be human generated for the purposes of sorting or gatekeeping on the internet, can detect cheating on essay assignments, and can be used as an automatic captcha that does away with the hassle of…
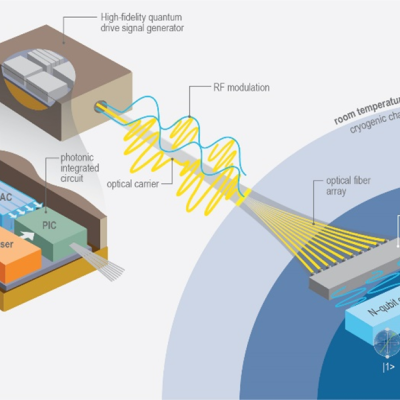
LLNL researchers in the NIF Directorate DoD Technologies RF Photonics Group explored phase modulation solutions to this signal processing challenge. Optical frequency combs offer phase noise characteristics that are orders of magnitude lower than available from commercial microwave references. The Photonics Group researchers recognized that by converting the intensity information into phase,…

LLNL has developed a new method for securely processing protected data on HPC systems with minimal impact on the existing HPC operations and execution environment. It can be used with no alterations to traditional HPC operations and can be managed locally. It is fully compatible with traditional (unencrypted) processing and can run other jobs, unencrypted or not, on the cluster simultaneously…

LLNL's Slurry Stabilization Method provides a chemical means of stabilizing a polishing compound in suspension at working concentrations without reducing the rate of material removal. The treated product remains stable for many months in storage.
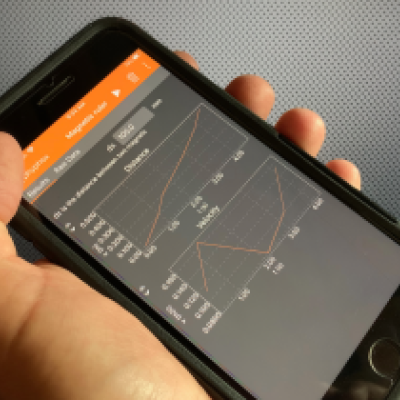
LLNL's NeMS system enables network mapping operations by using two LLNL-developed software systems: LLNL's NeMS tool and the Everest visualization system. Each software system can be also used separately for their specific applications. When the two systems are used together as an iterative analysis platform, LLNL's NeMS system provides network security managers and information technology…
