CSP-POST provides the capability to inspect all incoming and outgoing emails while providing after-the-fact forensic capabilities. Using commercially available lightweight and serverless technologies, CSP-POST easily collects all email and parses it into easily searchable metadata, enriched and ready for analysis. The web-based application is deployed in a repeatable, testable, and auditable…
Technology Portfolios

LLNL has invented a new system that uses public key cryptography to differentiate between human-generated text and AI-generated text. This invention can be used to validate that text is likely to be human generated for the purposes of sorting or gatekeeping on the internet, can detect cheating on essay assignments, and can be used as an automatic captcha that does away with the hassle of…

Lawrence Livermore National Laboratory (LLNL) is offering the opportunity to collaborate in accelerating artificial intelligence (AI) for applied science, including research in key areas such as advanced material design, 3D printing, predictive biology, energy systems, “self-driving” lasers and fusion energy research.
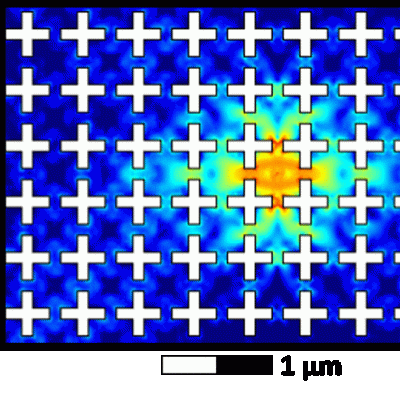
LLNL has developed a method of extending device lifetimes by imprinting into the device a shape that excludes specific vibrational modes, otherwise known as a phononic bandgap. Eliminating these modes prevents one of the primary energy loss pathways in these devices. LLNL’s new method enhances the coherence of superconducting circuits by introducing a phononic bandgap around the system’s…

Clinical images have a wealth of data that are currently untapped by physicians and machine learning (ML) methods alike. Most ML methods require more data than is available to sufficiently train them. In order to obtain all data contained in a clinical image, it is imperative to be able to utilize multimodal, or various types of, data such as tags or identifications, especially where spatial…

Some COVID-19 diagnoses are utilizing computed tomography (CT)-scans for triage. CT-scans produce immediate results with high sensitivity. The digital images produced by a CT-scan require physicians to identify objects within the image to determine the presence of disease. Object identification can be done using machine learning (ML) techniques such as deep learning (DL) to improve speed and…

MimicGAN represents a new generation of methods that can “self-correct” for unseen corruptions in the data out in the field. This is particularly useful for systems that need to be deployed autonomously without needing constant intervention such as Automated Driver Assistance Systems. MimicGAN achieves this by treating every test sample as “corrupt” by default. The goal is to determine (a) the…

LLNL has developed a new method for securely processing protected data on HPC systems with minimal impact on the existing HPC operations and execution environment. It can be used with no alterations to traditional HPC operations and can be managed locally. It is fully compatible with traditional (unencrypted) processing and can run other jobs, unencrypted or not, on the cluster simultaneously…

LLNL has developed a new system, called the Segmentation Ensembles System, that provides a simple and general way to fuse high-level and low-level information and leads to a substantial increase in overall performance of digital image analysis. LLNL researchers have demonstrated the effectiveness of the approach on applications ranging from automatic threat detection for airport security, to…
LLNL's NeMS system enables network mapping operations by using two LLNL-developed software systems: LLNL's NeMS tool and the Everest visualization system. Each software system can be also used separately for their specific applications. When the two systems are used together as an iterative analysis platform, LLNL's NeMS system provides network security managers and information technology…

