CSP-POST provides the capability to inspect all incoming and outgoing emails while providing after-the-fact forensic capabilities. Using commercially available lightweight and serverless technologies, CSP-POST easily collects all email and parses it into easily searchable metadata, enriched and ready for analysis. The web-based application is deployed in a repeatable, testable, and auditable…
Keywords
- Show all (206)
- Instrumentation (39)
- Additive Manufacturing (36)
- Sensors (16)
- Synthesis and Processing (16)
- Diagnostics (13)
- Photoconductive Semiconductor Switches (PCSS) (9)
- Electric Grid (8)
- Imaging Systems (8)
- 3D Printing (7)
- Materials for Energy Products (7)
- Carbon Utilization (6)
- Semiconductors (6)
- Compact Space Telescopes (5)
- Data Science (5)
- Therapeutics (5)
- Diode Lasers (4)
- Laser Materials Processing (4)
- Material Design (4)
- Optical Switches (4)
- (-) Cybersecurity (4)
Technology Portfolios

LLNL has invented a new system that uses public key cryptography to differentiate between human-generated text and AI-generated text. This invention can be used to validate that text is likely to be human generated for the purposes of sorting or gatekeeping on the internet, can detect cheating on essay assignments, and can be used as an automatic captcha that does away with the hassle of…

LLNL has developed a new method for securely processing protected data on HPC systems with minimal impact on the existing HPC operations and execution environment. It can be used with no alterations to traditional HPC operations and can be managed locally. It is fully compatible with traditional (unencrypted) processing and can run other jobs, unencrypted or not, on the cluster simultaneously…

LLNL's method of equivalent time sampling incorporates an embedded system that generates the pulses used to trigger the external circuit and the data acquisition (DAQ). This removes the external reference clock, allowing the overall system clock rate to change based on the ability of the embedded system. The time delays needed to create the time stepping for equivalent time sampling is done by…
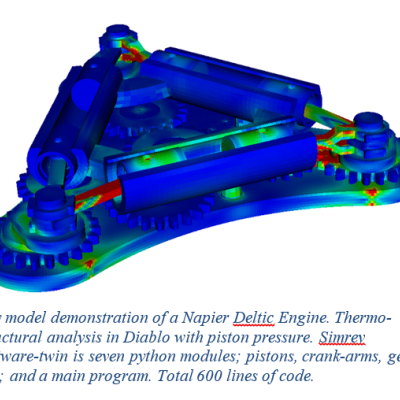
Simrev is a python library imported into a user-generated program. As the program grows in capability and complexity, the engineered product matures. The "software twin" handles all changes to product configuration and is the portal to running supercomputing analysis and managing workflow for engineering simulation codes. Assemblies become program modules; parts, materials, boundary conditions…
LLNL's NeMS system enables network mapping operations by using two LLNL-developed software systems: LLNL's NeMS tool and the Everest visualization system. Each software system can be also used separately for their specific applications. When the two systems are used together as an iterative analysis platform, LLNL's NeMS system provides network security managers and information technology…

