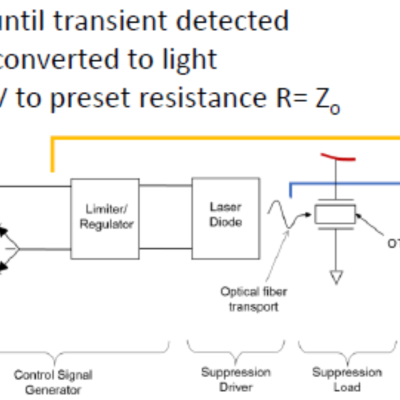
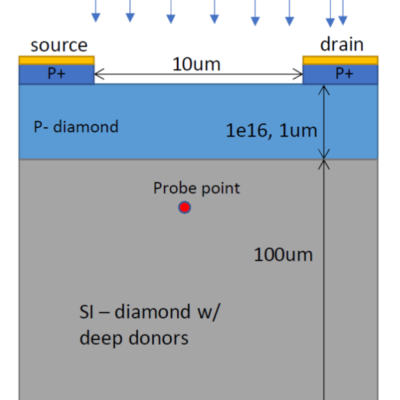
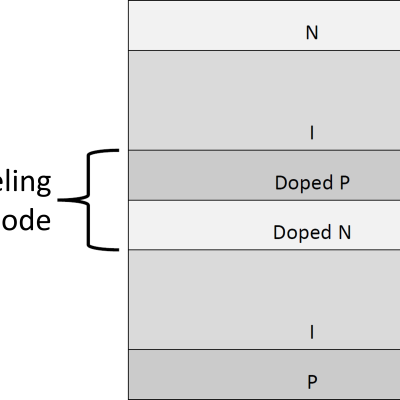
The approach is to leverage the fact that a momentary “load” equal to the power transmission line impedance, (Z0), during the transient can suppress its propagation. Z(0) is typically a fixed impedance of several hundred ohms based on the geometry of most single wire transmission lines.
So, an isolated self-powered opticondistor (OTV) system may provide an ultrafast method of…